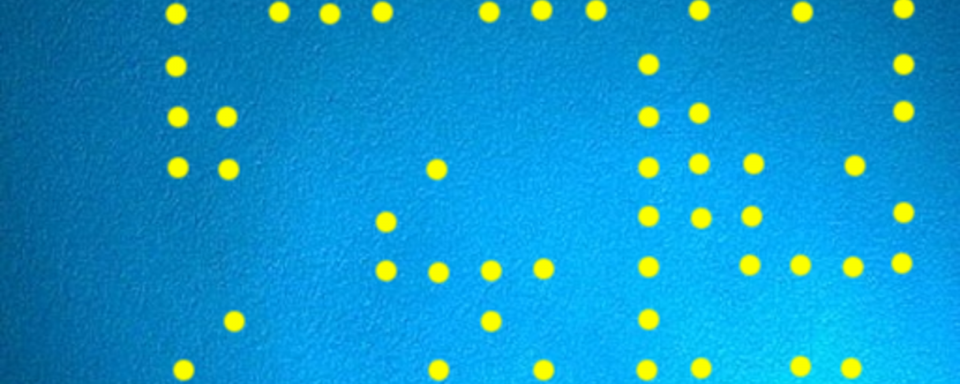
Early June, agents from FBI were investigating about a top secret document that was supposedly leaked to the press. While carefully examining the document, they noticed there were creases that proved the pages were printed and manually transferred. After this incident, experts began to study the document carefully, which is now made available to the public on the web. Something else of interest was discovered: there were yellow dots (secret tracking dots) in a rough rectangular pattern present repeatedly throughout the page. It formed a coded design or pattern and was hardly noticeable to the naked eye.
All About Secret Tracking Dots of a Printer
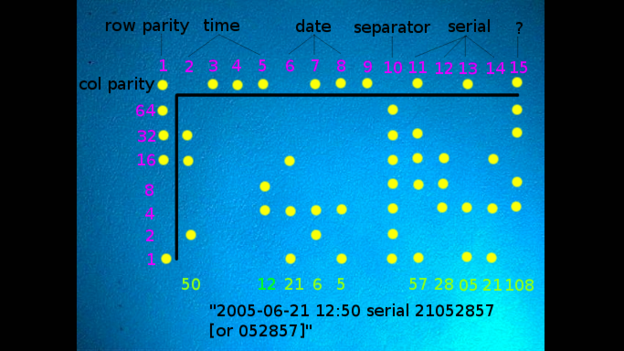
After analysing it quickly, they were able to reveal the exact date and time the particular document was printed or at the most, the time according to the printer’s internal clock at the moment that document was printed. A serial number of the printer was also encoded through those dots. These dots, also known as “microdots” are known very well by security researchers. Most of the colour printers make an addition to the documents printed by them without the knowledge of the person using it. The person never knows of the existence of these secret tracking dots on their document that they have just printed.
In the case that the FBI was investigating, they did not reveal to the public that they were able to identify their suspect with the help of these secret tracking dots. But the fact that these microdots were present on a highly confidential document has generated much interest and curiosity. Ted Han from the cataloguing platform Document Cloud said that these secret tracking dots were quite obvious after zooming in on the document. Han was one of the first to notice them and found it interesting and outstanding that there exists such technology in our world today.
Rob Graham, a blogger who has published a blog on how to identify these microdots and decode them, made another observation. He said that their positions when compared with a grid, give specific details like hours, minutes and numbers. These secret tracking dots have been in existence since a number of years. A list of colour printers that are known to use them has been maintained the Electronic Frontier Foundation (EFF).
Microdots are not only an area of interest to spies, but also have other potential uses, as stated by Tim Benett. Benett is a data analyst at Vector 5, a software consultancy, and was of the persons who examined the leaked document. He also stated that these secret tracking dots could be used to determine forgeries. He explained further that if someone says a document is from 2005, with the help of the microdots on the document one could determine if the document is really of that time. The EFF has an online tool available which will help decode the information the pattern holds if one comes across a document that contains these microdots.

Secret Tracking Dots Concealed Messages
Similar types of secret messages hidden right under our noses, also known as steganography, have been around for quite some time now. A bit more famous than the microdot, the Eurion constellation, which is a unique five-point design, is featured in many banknotes from across the world. In order to refrain from counterfeiting, when this pattern is recognised by the printer or scanner, they are programmed to refrain from producing copies of the banknotes. The National Security Agency or the NSA gives us an interesting example of secret tracking dots with a hidden message and that is from the World War Two. German Spies from that era had an envelope which had tiny dots taped inside and concealed a memo, which were meant for their contacts in Lisbon.
During that time, these spies worked undercover in acquiring materials from Germany such as radio equipment and secret ink. However, these messages were intercepted by the Allies and their mission was disrupted. The Germans used these tiny dots usually in the form of mere bits of unencrypted text which was squeezed down to the smallest size of a full-stop. This form of communication was largely used during the WWII and later during the Cold War. There are also reports of Soviet Union agents operating undercover from their base in West Germany, using letter drops to convey their messages in this manner.
In today’s age, microtext can be used by anyone who wants to safeguard their property. Companies such as Alpha Dot in the UK, sell small bottles of adhesive that is permanent, filled with dots that are the size of a pin-head. These dots are covered in microscopic text holding a unique serial number. If a stolen item is retrieved by the police, the owner can be verified by matching this serial number. There are many examples of these tiny messages that do not necessarily have an output in the form of a coded design developed from a printer but they are a very good example of how a small message applied physically to any document or object can be traceable and identified.

Some forms of steganography that are based on text, are completely devoid of alphanumeric characters or symbols. A security expert at the University of Surrey, Alan Woodward, gives us the example of Steganographic Nature Of Whitespace or SNOW. He explains that this technique puts spaces and tabs where lines end in a piece of text. With the help of the exact number and order of these blank white spaces, a hidden message can be encoded.
Few organisations, such as the NSA, have maintained records of every document that has printed along with having methods to track down their document once its printed. They are aware that people have the knowledge of these secret tracking dots and so don’t fully depend on this method for tracing their documents. Whether it is ethical for printers to be adding these secret tracking dots to documents without the knowledge of the user is a long ongoing debate. There has also been a suggestion that is a kind of a human rights violation. However, it is believed by many that this use is ideal for maintaining secrecy for confidential and classified documents as it is mandatory for some cases.