What is Pretty Good Privacy and Public PGP Key?
This one is actually one type of encryption system. People use it to send encrypted emails and encrypt sensitive files. It was invented in 1991. Therefore, the software becomes the de facto standard for email security. Generally, the fame of Pretty Good Privacy depends on two factors.
The first factor is that people got the system originally available as freeware. Multiple people prefer to use this software. It is used among those who wanted an additional security level for the email messages.
The second factor is that the software enables its users to send encrypted messages to each other. Hence, the users don’t need to exchange private encryption keys. It happens as the software uses both symmetric encryption and public-key encryption.
How does Pretty Good Privacy Work?
The software usually shares a few features along with other encryption systems such as Kerberos and SSL encryption. People use the Kerberos software for authenticating network users. On the other hand, people use SSL encryption to make their websites secure.
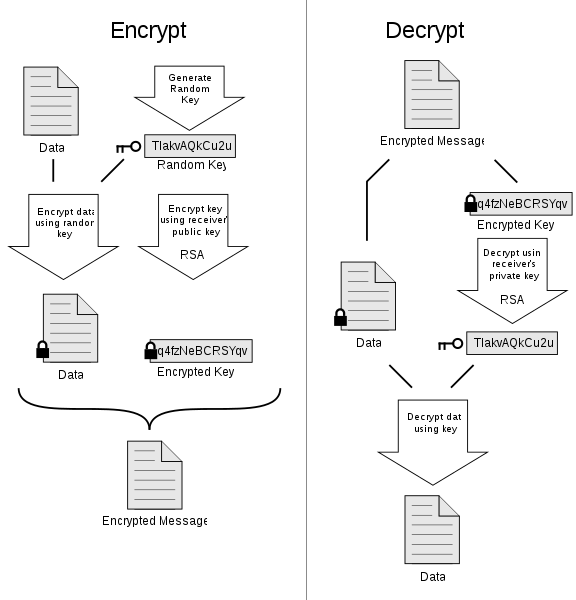
This one uses basically two forms of encryption that are symmetric key encryption and public-key encryption.
Here, we have given the method that lets you know how it works.
First of all, this software creates a random session key. To generate this, it uses one of the two (main) algorithms. What it creates is a huge number. You can guess this. It can be used only one time.
After that, it gets encrypted. You can do this by taking the help of the public key of the intended recipient of the message. Anyone is able to use these as a message.
Now, the second one will send the encrypted message with the help of private. Besides, you can even decrypt the real message using it.
Why would we encrypt the encryption key itself?
The answer is very easy. In general, the public one’s cryptography is quite slower than symmetric encryption. When you will use any symmetric encryption, you can send the encryption to the recipient in plain text. This process may not be secured. When you use the asymmetric system to encrypt the symmetric one, the efficiency of this is combined with the security of asymmetric cryptography.
Example of PGP Encryption in Action
In practice, you can send a pretty good privacy encrypted message easily. For instance, you can take ProtonMail. It supports the software natively. Here, you need to choose Sign Mail to encrypt your email. After selecting it, you can see a padlock icon. This one is available on the subject line of their emails.
ProtonMail usually hides the complexity of the encryption and decryption of the message. It also works similarly to how other email clients offer the software. However, you should send the public key first to the users when you will communicate with the users outside. They sent the message in a more secured way. And both sender and receiver need not worry about the complexities involved in the process of encryption done.
Uses:
Generally, there are three primary uses of this software that follows:-
To send and receive encrypted emails.
Verify the person who has shared the message with you.
To encrypt files that are stored on your devices or in the cloud.
The most dominant use of the software among these three is to send secure email. However, let’s have a look at the points.
Encrypting Emails
Most users prefer to use this software mainly to send encrypted emails. In the previous days, activists, and journalists used it. Besides, it was used also by those people who prefer to deal with sensitive information. It was Paul Zimmerman who was the original designer of this system. He was a Peace and political activist. Later on, he joined Startpage that we know as a very famous private search engine.
Nowadays, the software has become more famous. Multiple people now prefer to use this system for keeping personal information safe. It is because they have realized the amount of information that the corporations and their governments are collecting on them.
Digital Signature Verification
On the flip side, what makes it attractive is that people can use this for email verification. Sometimes, journalists are unable to identify the person who sent a message to them. In those cases, they can use the Digital Signature along with the system to verify 55mm
The digital signature follows an algorithm to work. According to the algorithm, you need to combine the sender’s key with the sending data. This method creates a “hash function.” It is one of the algorithms using which you can transfer a message to a block of data of fixed size. You can encrypt this sometimes with the help of the sender’s private key.
Then, the message is decrypted by the recipient of the message through the sender’s asymmetric key. The recipient can know even if you want to convert one character of the message. It indicates that the message cannot tampered with fake digital signature.
Encrypting Files
Encrypting files is the third use of this software. It encrypts files in a highly secured way as it usually follows the RSA algorithm. This algorithm is quite unbreakable. The software offers more security while using this alongside a Threat Detection and Response Solution. The algorithm used by this software is so secure that you can use it in high-profile malware. CryptoLocker malware is an example of high-profile software.
Symantec acquired the corporation back in 2010. From that time, it has become the dominant vendor of this encryption software via products like Symantec Encryption Desktop and Symantec Encryption Desktop Storage. It offers encryption for all types of your files.
Do I Need Pretty Good Privacy Encryption?
It relies on the amount of security the user wants for his or her files. The PGP users need to do little more work when sending and receiving messages using this encryption to improve resilience of their system attack.
Let’s have a look at this closely
Pros of the Encryption
The algorithm used here makes this encryption security software unbreakable. It is the prime benefit of private software. This software is considered the best way to improve cloud security. In simple words, whether it is a hacker or NASA, it is quite impossible to break the encryption.
However, a few EWS stories are there which point out security flaws in the implementations of this software. For example, they point out the Efail vulnerability. You need to recognize that the software is very secure still.
Cons of the Encryption
One of the main disadvantages of the software is that it isn’t user-friendly. Using the software, you can add additional work and time to the daily routine. Besides, people who usually use the system have to know how the method works. Sometimes if the encryption is not done properly then it will lead to security loopholes in your message.
It indicates that those businesses which want to use the software need to provide training. Due to this reason, multiple businesses are there which prefer to use alternatives. You can get encrypted messaging apps. For example, Signal is an app that offers encryption which is much easier to use. If you want to store data, then choose anonymization as an alternative. It is a nice alternative for encryption.
Lastly, you should know that private software encrypts your messages. But it won’t make the user anonymous. A few anonymous browsers are there which use proxy servers or you need to use them through VPN. Thus, you can easily hide your true location, trace emails sent through this software to a sender and recipient. While sending the encrypted message the subject line is usually not encrypted. Therefore you should not share sensitive information in the subject line.
How Do I Set Up PGP Encryption?
When you are going to set up the encryption, you have to download an add-on for the email program. After that, you need to follow the installation instructions. Multiple add-ons are available there for Thunderbird, Outlook, and Apple Mail. You may notice the increase in the number of users of online email systems in recent years. In these cases, Pretty Good Privacy software is by default.
Many people want to use security software for encrypting files. A huge number of large-scale software solutions are available in the market. Symantec is a good example of it. This one provides PGP-based products like Symantec File Share Encryption. It helps to encrypt files shared across a network. Symantec also offers Symantec Endpoint Encryption used especially for full disk encryption on phones, desktops, and removable storage.
Unzipping and installing the PGP software
First, you need to download the software. As soon as you complete the download, you will get the zipped version available on the hard drive. After that, your job is to unzip the file. In this case, what you can do best is to use the shareware WinZip. You need to install this on the PC. However, sometimes you can have the program already installed on the PC while installing other software. Check whether you have the WinZip program or not. Hence, you need to click two times on the downloaded file named Pretty Good Privacy software FW658Win32.zip.
In case you don’t have the WinZip installed on the computer, download it from the web. It is the best thing you can do when you have any doubts. You can go to their site
There, you need to follow the guidelines for installing the software on your desktop. Now, you can unzip the file and install it. The steps you need to follow is as follows:-
First, you need to find the zip file of the software PGPFW658Win32.zip on your computer. Then, you need to tap two times on it for unzipping the file.
Pretty Good Privacy Setup Process
After that, you have to run the Setup program. It will begin instantly after running the program. Then, you can see the PGPFreeware 6.5.8 Setup Wizard.
Now, you need to follow the step-wise guidelines of the Wizard. Then, you have to press the Next button. You can see the first three-screen asking about the Pretty Good Privacy software. Go through the details carefully and then tap on the Next button.
After that, the 4th screen you get to see requires your name and the company’s name you are working.
Now, you need to confirm that the folder you have downloaded at its position. Then, you need to install the program. If you don’t have any idea, go with the default for this item.
It asks you what components you prefer to install. There is no necessity to install the PGPnet Virtual Private Networking. It is because most people don’t prefer to use this. On the other hand, it can cause nasty network configuration issues. That’s why you should deselect the item. Remove the checkmark that is available near it before tapping on the Next button.
Go through what the Wizard wants to say on the ensuing screen. When you are asked to choose, you need to accept the defaults. Permit the wizard to make the setup job done for you.
As soon as you install the software, you need to reboot the system. The software helps you in this case by allowing you to go ahead and Restart.
When you can restart your system, you can generate your Public and Private Keys.
Creating Your Public and Private Pretty Good Privacy Software keys using wizard
Now, you have the software installed on the PC. Therefore, you can make a Public and Private Key pair easily at any moment you want. It means you are willingly sharing your public key with your recipient of your mail. Which carries the secret information you are sharing?
The Private Key you have is considered as so-called because it can decode any details encoded with it. So, it is better for you to keep the details of it limited to you. Thus, you can secure your privacy. To do this, you need to follow the steps:-
First of all, you need to go to the PGP keys. Select the option Start/Programs/PGP/PGPkeys or tap on the PGPtray icon to open it. You can get this available at the lower right corner of the screen. Then, you have to choose which is available in the pop-up menu.
Then, the window opens up and displays multiple names in the list. You can see the name of yours and others which you have selected to add to the list.
Now, you can see the menu bar. Tap on the Generate New Keypair option to get the Wizard. Then, you need to go through the introductory dialog and tap on the Next button.
The Wizard wants you to put the name and email address. You can put any name here. It’s better for you to put the original email address to get the benefit of this feature. After entering the name and email address, you need to tap on the Next option.
After that, you need to choose the type of key that you want. You can accept the default (Diffie-Hellman/DSS) option. Then, tap on the Next option.
Then, what you have to do is to specify a size for the latest keys.
How Generate Private & Public PGP Key Wizard Setup
After that, you need to accept the default option again. Then, you need to tap on the Next option.
Now, the wizard asks you the time when you want the key pair to be expired. In this case, also, you have to accept the default option and then hit the Next button again.
After that, your job is to put a passphrase. Think deeply before doing this. You need to select any passphrase which contains a minimum of eight (8) characters. Eight characters are the lowest requirement. The paraphrase should include a mix of upper and lowercase letters or other characters. The more you mix characters, the longer paraphrase you can make.
Now, put the paraphrase what you have decided. Next, you have to press the Tab. Then, you need to enter it again to confirm. Now, your job is to tap on the Next again.
In case you have put a wrong passphrase, you will get a warning from the Wizard. Then, it asks you to return and re-enter other passphrases. But if the process is okay, then the wizard can generate the key pair for you. You may need to move the mouse or tap random buttons. It will help the wizard to generate a more secure key. Now, you need to tap on the Next option.
Now, you will be asked whether you want to send the latest generated key to the globe or not. If you allow it, then other people can find and use this whenever they want to encrypt data. However, it is not mandatory. So, if you want, you can tap on the box only. After that, you have to tap on the Next option once more.
Changing your Passphrase
After some time of using the software, you may want to change the passphrase. You may especially want to change it when the previous one is not so complex. You can change the passphrase very easily.
Here, we have given a process that you can follow to change the Passphrase.
At first, you have to do the same as you have done before in the first step of the setup process.
Now, you have to highlight the key which you prefer to replace. Then, you need to go to the menu option and choose the Properties.
After that, you can see a button in the dialog box for changing the passphrase. This box is popping up on the screen. Now, what you have to do is to tap on the Change Passphrase option. Then, as usual, you need to enter the current Passphrase you have. After entering the passphrase, you have to tap on the OK option.
Next, your job is to decide on a new passphrase. If you think that you can forget it, then the best way you can do is to write down the passphrase. Then, you need to write the word “DESTROY” or “BURN” in large letters.
As soon as you become ready, you need to put the passphrase in the New Passphrase dialog box. Then, you need to confirm the latest Passphrase entering this again. Next, you have to tap on the OK option.
Distributing the Public PGP Key
Want to replace the Public Keys with any individual or group of individuals? The best way you can follow is to send it via email to whom you want to give it.
The recipient needs to install the software if he or she wants to add your key to his or her keyring. He needs to install the software to use to encrypt the data that he wants to send you. Similarly, if you want to send encrypted data to anyone, you should also have his or her key. It may seem to you as tricky at first.
Anyone who uses the Pretty Good Privacy software has two keys— public and private. Other people use the public one to encrypt the information that they want to share with you. In this case, you are the one who gets to know the information only. On the flip side, when someone sends you an encrypted message, use the Private Key to decrypt it.
The main thing is that it is only you who is able to decrypt the secret message. It is because you have the private one only along with the passphrase. Therefore, you can unlock it only. If you share the private one and passphrase with someone, then it is of no use.
Whether you want, you can put the public one on one or more than one server. Thus, it can form an international server chain. But doing this allows everyone in the world to exchange secure communications with you.
How to Add an Email Message:
If you want to add it to an email message, then follow these steps underneath.
First, you have to follow the first step that is already given in the setup process.
Then, you need to find the key pair available in the list in the box. Next, you need to copy this. Use the control-C button to do this.
Then, you need to write a new message in the e-mail editor which is available in the To: box. Now, you need to put the e-mail address of the recipient. Then, your job is to write a subject header. You can type “My Public Key” as a header.
After that, you have to click to get the cursor available in the email body. As soon as you get this, you need to paste the key you have. Use the Control-V button in this case. Then, you need to send this.
Making your Public PGP Key available through a certificate server
You can keep this on the certificate server. It is a kind of server that any person is able to get access to. Using this, they can even send you encrypted messages. But you don’t need to worry about your privacy being compromised. However, whether you are a beginner to the Pretty Good Privacy software, you must not want to do this at this moment. It is because you may want to exchange at a later date. The main thing is that you are unable to remove the key after putting it on a certificate server. Therefore it is advisable not mess the server with keys that are not used.
That’s why you need to keep in mind this part later on as this can be beneficial for you.
Here, we have given simple steps to make the key available through the certificate server at MIT. The type of server doesn’t matter in this case. Wherever you will post, people worldwide get this available.
First, you need to connect this to the internet so that the software can access the website. You can send the public key to the website.
Follow the first step of the set-up process as usual.
Now, you can see an icon on the list in the window. It represents your Public Key which you want to post to the certificate server at MIT.
After that, you have to pull down the Server menu. Then, you need to select the Send option. Next, your job is to choose the link to the MIT server at http://pgpkeys.mit.edu:11371.
The software can access the server now and post it there. After doing this, it will inform you that you have posted it successfully.
Obtaining and Adding someone else’s Public PGP Key to your keyring
You can follow two simple ways. What you can do is that you can send it via email and then you need to paste this into the keyring from the e-mail. Secondly, you can get it if these are posted already on the certificate server.
In this case, your friend needs to follow the previous step.
Here, first, you need to go to the specific email message and open it.
Then, drag to select an area from the —–BEGIN PGP PUBLIC KEY BLOCK—– to —–END PUBLIC KEY BLOCK—–.
After that, you need to copy this.
Then, do the same process that you have done before in the first step of the set-up procedure.
As soon as you see the window, you need to paste it for adding to your keyring.
Using the PGP encryption software to send (encrypt and sign) and receive (decrypt) secure emails
Here, you get to know how you can encrypt messages or decrypt messages.
First, follow the encryption process.
Here, you need to compose the email first in your preferred language. Choose
French, English, Spanish, German, etc. anyone of these you want.
After you finish composing the email, you have to ensure that the cursor should be in the body of your message. Now, you need to tap on the icon. It is available in the lower right corner of the screen.
Quick Setup:
You get to see a Current window in the pop-up menu. After that, you need to go to the submenu that is available in the Current Window. Then, choose Encrypt & Sign. When you select this, you can see the Selection dialog box that contains the list of Public Keys. You should know that a private keyring is such a place where the private keys are stored.
This one is encrypted only with the passphrase you have chosen. It is because if by chance anyone gets the access, he or she can’t use this. The software needs access each time. That’s why you need to enter the passphrase every time. The benefit here is that the software remembers the cache for two minutes. As a result, when you are going to use it again within two minutes, you don’t need to re-enter.
Tap two times on the person’s key to whom you want to send your message. After making your selection, you have to tap on the OK option.
Now, you need to enter the passphrase. Write this with care and then you have to press the OK option. If all things will be okay, your message gets converted to gobbledygook. The ciphertext looks like this:

Now, you share the message as you do usually.
Decryption Process:
Go to the email that contains the encrypted message. Here, you can see the unintelligible ciphertext.
Drag your cursor for selecting the block of ciphertext.
You need to tap on once more on the icon. It is available in the lower right corner of the screen.
Now, choose the Decrypt & Verify option as you have done before for the case of encryption. Then, you can see the dialog box. You need to enter the passphrase there.
Next, you have to write the passphrase into the software. Now, you can see the box popping up on the screen. Then, you need to tap on the OK option. The decrypted message displays a new window in front of you. If you want to keep this window version, then copy & paste it into your preferred word processor. Before saving it to the disk, you must paste it there. The decrypted message looks like this:
#“*** Pretty Good Privacy software Signature Status: good
*** Signer: Robert A. Rosenberg <[email protected]>
#*** Signed: 06/30/2001 at 00:51
*** Verified: 06/30/2001 at 00:52
#*** BEGIN PGP DECRYPTED/VERIFIED MESSAGE ***
This is a sample of what the above Encrypted&Signed message looks like After it has been decrypted and the signature has been successfully verified. Since the Public Key that was used to encrypt this text belongs to Robert Rosenberg, only he can decrypt the message to extract this message. An Encrypted&Signed message is a Clear Signed Message (such as the sample in Step 10 below) prior to the Encrypt Stage and after the Decrypt Stage. While it is possible to just Encrypt a message, it is usual to also sign it to prove its origin.
*** END PGP DECRYPTED/VERIFIED MESSAGE *** ”
Using your Default Public PGP Key to save a backup, encrypted, decipherable copy of all your e-mail messages
After you encrypt a message with the help of the Public Key of the receiver, you are unable to decrypt it. Even, you can’t read the message because you don’t have the correspondent’s Private one. However, it doesn’t matter as you don’t need to keep a copy of the message that you send every time. But sometimes, it becomes essential for you to keep a copy of your own message for the record purpose. You need to decrypt the message in case you want to read this later. The best thing you can do in this case is to tell the Pretty Good Privacy software to encrypt all messages. Here, we have given the procedure of how you can do it.
First, do the first step of the setup process.
Then, you need to go to the Edit menu. After that, you have to select the Options.
Now, you need to select the General tab that is available in the Options dialog box.
You have to tap for putting a check mark m in the small box. After that, you need to tap on the OK button.
It takes care of all the encrypted copy of messages which you may want to decrypt at a later date. Now, you need to sign and verify Clear Signed emails. To know how to do this, see the next step.
Pretty Good Privacy software signing your own unencrypted emails
Sometimes, during communicating you may not want to use the encryption. For instance, when you share your notes with your friends, you are not sure whether each member is using encryption or not. During that time, it is better for you to not encrypt your post. What you can do is to sign your posting with the Pretty Good Privacy software encrypted signature. This signature can be verified by other users also.
When they verify this, it assures that it is you who send the note. The notion of offering added assurance to the source of communication is a part of the “Web of Trust”. Here, people usually verify and sign carefully to reassure them that the originator is the one who appears to be.
Pretty Good Privacy: Sign in to Unencrypted Mail
Here, we have given easy steps that you can follow to sign the unencrypted mail.
As soon you finish writing the email, you need to right-click on the PGPtray icon. You can get this available in the lower right corner of the screen. Then, you can see the pop-up menu. After that, you have to select the Current Window/Sign. It is fed into a HASH Function.
Now, you have to put the passphrase. However, you can extend the time of the cache also to keep the passphrase for more time as cache memory.
After that, you need to enter the Passphrase and then you have to tap on the OK button.
It is all about signing unencrypted emails. But it is unfortunate that only signing the unencrypted mail can’t make the receiver sure who you are.
That’s why it is essential that the public key you have, needs to be signed at least by one whom you trust.
It indicates the identity of your “real world”/”Offline” with “Electronic”/”Online” persona. As long as all the messages are signed using the same one, it is the “proof” of electronic identity.
Digital Notary or Digital Signature
You need the signing only when you have to do the real-world linking. This Signing of an Email is the proof that works as an additional purpose. It shows that the owner has written the message and it is not altered between the time when the owner signed this and when you verify the signature. It is not altered till the signature has been verified.
You can know that the message was signed from verification. Thus, you get to know the latest time when it is written. However, it is valid for theory only as there is no proof of the validity of the stamp. As proof of the time accuracy is vital, you have to apply some external function. For example, you can apply the Digital Notary as the message or Digital Signature.
Here, we have given the actual signing process which follows:-
When the message gets fed into a Hash function, it generates a string. This string helps to represent the contents of the message. It is called the Message Digest.
You can create a string easily. Just you need to change the format of the message. For example, you can move a letter or word between the ends of one line or place it at the start of the next. Thus, you can make a different string with ease. You can even create a different Message-Digest by altering the actual contents also along with its formatting.
After that, the Message Digest needs to be encrypted with the time stamp and other control information. It helps to generate the Digital Signature that you can place after the message text. It is the text part that you can see in an encrypt and sign operation.
Sometimes, the message seems to be not signed clearly after decrypting but was encrypted. You need to then decrypt the Digital Signature using the recipient’s Public Key for recovering the Message Digest. You need to remember always when you encrypt a message using a private one, it allows you to decrypt with the corresponding Public one.
Hash Function and Message Digest:
Next, you can see the message itself fed through the Hash Function. Thus, it can generate another Message Digest.
When both the two messages get matched, make sure that the message has not been altered. You can confirm from here that it is the owner who has sent the message.
As soon as you complete the verification step, the message will get altered. Now, you can see a block of text displaying the status of the verified operation. You will get the option that asks if you want to replace the received signed copy with the verified copy. You don’t need to do this as you don’t want to alter the message after receipt and verification. Now, keep this in the Signed/Un-Verified form. It enables you to verify again at any time you want.
Using the PGP Encryption Software to Protect (encrypt) your personal documents
You obviously have personal documents on your computer at home or in the office. You must not want to share these documents with other people. So, it is important for you to use your own public key for encrypting these documents. You are able to encrypt any single file or a set of files very fast. When it comes to decrypting, you only need to reverse the process. Just select the Decrypt option instead of selecting Encrypt from the software menu.
Pretty Good Privacy: Encrypt A Single File
The steps which you need to follow to encrypt a single file or document is as follows:-
First, you have to go to the Start menu and then right-click on it. You can get this option available in the lower-left corner of the Windows screen. Next, you have to choose the Explore option which is available in the pop-up menu. Then, choose the C drive(for instance). It is available in the left-hand column of the Explorer window. Then, you get to see the contents of the drive which are listed on the right side of the Exploring window.
Now, you have to right-click on a document that you want. After clicking on this, you can see a new item that is available in the pop-up menu.
Next, your job is to choose the Pretty Good Privacy option from the pop-up menu. Then, a sub-menu appears in front of you which enables you to encrypt the highlighted document. Tap on the Encrypt option.
After that, you can see the Key Selection dialog box. You have to tap on the key two times. Then, you need to hit the OK button. After clicking on it, the software has produced a second version of the document with the help of a .pgp extension.
If you want to remove the original, non-encrypted document, then right-click on the original file. Then, choose the Delete option available in the pop-up menu. Thus, there exists only the encrypted file that you can read-only.
Pretty Good Privacy: Encrypt Files and Folders
Here, we have given the steps for encrypting a selected set of files or documents in a folder.
Start as you have started in the previous process while encrypting a set of files.
If you think, you can open the folder where you want to save the files for encryption. Besides, you can drag all these files for selecting them as a group. You can first select the first file of the list and then hold down the shift button also.
Now follow the previous procedure again from the 3rd step to the 5th step.
The non-encrypted file should be selected as a block. In case these aren’t, you only need to tap on the Type header. You can see this option available at the top of the Explorer window. With the help of this option, you can sort all the files as encrypted and unencrypted. Now, right-click on any of the original files which are highlighted. Then, you need to tap on the Delete option available in the pop-up menu.
If you want, you are able to both encrypt and decrypt the complete content of any folder. For this, you only need to right-click on the folder. Then, you have to choose the Encrypt option that you can get in the PGP sub-menu. However, it is not so easy as you can open the folder first and choose files before encrypting. It is because you need to delete the files one by one after the completion of the encryption procedure by the Pretty Good Privacy software.
How to Generate Public PGP Key on Windows
Here, we have given the following guide that contains the detailed instructions for generating the software key-pair.
At the end of the procedure, you will get a Pretty Good Privacy public and private key-pair on the PC.
Installing Gpg4Win
First, you need to download the Gpg4Win. Go to the www.gpg4win.org site and download it.
After that, you need to tap two times on the downloaded file. It will help you to install the application.
Next, your job is to open the Start Menu. Then, you need to launch Kleopatra. It is a Pretty Good Privacy keychain manager application.
Generating a Public PGP Key-pair
As soon as you install Gpg4Win and run Kleopatra, you can make the first key-pair of the software.
After that, you have to tap on the File option. Then, click on the New Certificate.
Next, you need to choose the ‘Create a personal OpenPGP key pair’ option.
Now, your job is to put your name and email address on the form.
Then, you have to review the settings. Now, if all the things are right, then hit the ‘Create Key button.
After that, you need to choose a strong passphrase. It helps you to give protection to the private key available on your hard disk with encryption. Keep in mind that you must not use your old password again. Instead, you should select a brand-new passphrase. Choose such one that you use never on any platform.
In case you get success in generating the key, you get to see the following options.
At last, you have to tap on the ‘Finish’ option for finishing the process.
Setting an Expiry Date
Now, you need to try to set an expiry date on the keys. Setting the expiry date will help you to avoid your key to be compromised and setting the expiry date will limit the lifetime of the public and private keys.
Now, you have to open the Kleopatra again.
Then, you need to tap on the software key-pair. Next, choose the ‘Change Expiry Date…’
Now, you need to set the time to two years as the expiry period. Then, you need to tap on the ‘OK’ option.
You need to set the expiry date.
Backing up the Public PGP Key-Pair
You should always make a backup of it. Thus, you can make sure that you can restore it. Backing up also ensures that you will get access to the encrypted emails. It is very beneficial when your pc or desktop is destroyed or gets stolen.
Then, you have to click right-click and choose the ‘Export Secret Keys…’.
Now, you need to give a name to the file as well as the path for the backup. Then, you have to tick on the ‘ASCII armor’ box.
If you complete the file successfully, the backup secret will save into a file.
Next, you have to back up the public key
Now, you have to right-click and then choose the ‘Export Certificates …’ option.
At last, your job is to copy both files— public and private to other off-site locations. You can store it in an external USB drive, a Dropbox folder. If you want, you can print this item on a piece of paper.
Pretty Good Privacy Encryption Software
Before going to use the encryption software, it is essential for you to download a piece of software first. It helps you to keep the method going by automating the process of encryption and decryption. You can get to see multiple products available in the market. But you should know about the one you are looking for.
How to Select Pretty Good Privacy Software
The main objective of using pretty good privacy software is to ensure the security of your message. While choosing this software, the first thing you need to be concerned about is security. We know this software as unbreakable. But a few examples are there where you can see vulnerabilities. If you are an experienced coder, it will be easier for you. Otherwise, you won’t spot the vulnerabilities. So, the best way you are looking for is to check the vulnerabilities in the software that you are using.
However, selecting the Pretty Good Privacy software depends on the personal or business requirements of every person. If you need to encrypt all your mails then using downloading and using an addon is cumbersome. And Pretty Good Privacy is a best solution.
Instead, what you can do is select an online Pretty Good Privacy service for sending vital emails.
At last, you need to select a software provider who is able to offer dedicated support. It can support through a customer support team and a user community. Sometimes, you may feel frustrated while learning to use the software. It is because it was the first time when you navigate the system. During this period, you must need help.
Different Pretty Good Privacy Solutions
There are a few different solutions to this software. But it relies on why you need to use this software and how often you have to use it. Here, we are going to discuss what most people want from this software. A few prefer to secure email. The five solutions to implement the software on the home or business networks.
-
Outlook with gpg4o
Gpg4o is a very famous solution of the Pretty Good Privacy software for Windows users. This software wants to integrate with Outlook 2010 – 2016.
Pros: It provides simple handling of emails. Most people who use windows can get the easiest and most user-friendly Pretty Good Privacy add-on here.
Cons: It is made up of the OpenPGP standard. This one is an open-source standard that is available for scrutiny. But the add-on is proprietary. Besides, the business license is very costly, i.e. near about €56.36.
-
Apple Mail With GPGTools
If you are a Mac user, then it is the right choice for you. It is the standard implementation of Pretty Good Privacy encryption. GPGTools is actually a suite of software which can encrypt all the areas of a Mac system.
Pros: The alternative can integrate with Apple Mail properly. It provides you a key manager which enables you to use the software in almost any application. With the help of this, you can use the command line
Cons: We know that it is the simplest way for Mac users. But if you use the encryption for the primary email, it can slow down the performance.
-
Thunderbird With Enigmail
The main objective of the design of Enigmail was to integrate with any particular email client. Thunderbird is taken as an example in this case.
Pros:
The main benefit is that the add-on here is platform-independent. Besides, it is completely free and open-source. The software is updated daily. In addition, the development team reacts quickly to respond to identified instances of malware.
Cons:
No dedicated support is with Enigmail, though the user community is quite big as well as active in this case. But it have plenty of reference material available.
-
ProtonMail
It is known as one of the first secure email providers. This one is very famous as a solution. You need to operate it through a web portal. It indicates that this one allows you to separate it from your everyday inbox.
Pros: It uses encryption for messages sent between two people automatically. It is User friendly. And very easy to setting up PGP.
You can use services such as Hushmail, Mailfence, etc. These work similarly and can send the occasional encrypted email easily. Hence, you don’t need to reset the entire system.
Cons: As ProtonMail sometimes implements the software via JavaScript in a website, a few people don’t regard it as completely secure. However, later on, ProtonMail maintains the security of the system very tight.
-
Android and FairEmail
This FairEmail can extend the encryption to Android phones. It is a stand-alone email app that is free to use.
Pros: If you are an android user and looking for the simplest solution, then it is the right choice for them. It offers the option of encrypting messages instead of doing this by default. As a result, you can select what you want to encrypt.
Cons: In this case also, the user community is quite small. It is because the use of the software through Android is rare.
How to verify PGP signature of downloaded software
If you are a Linux user, then you can easily install the software securely from the distribution’s repositories. But sometimes you may need to download software from the website. Then, who will give you the security that the software is secure enough?
A few software authors sometimes sign software like GPG with the help of this software program. GPG is a free software implementation of the OpenPGP standard. With the help of GPG, the integrity of software can be verified.
Procedure:
The process is quite easy:-
First, you have to download the software author’s public key.
Then, you need to check its fingerprint to make sure that this one is the right one.
After that, you have to import the right one to your GPG public keyring.
Next, your job is to download the signature file of the software.
At last, you need to verify the Pretty Good Privacy signature. Whether you get the signature correct, then ensure that it wasn’t tampered with.
Conclusion:
The software is safe and secured only when the private key remains private. If someone gets this, he or she will read all of your private things. It depends on how much security you want. You can keep it on your hard drive or any other place where there exist more security layers. Besides, you can keep it on a secure form of removable storage such as an encrypted USB drive.
Frequently Asked Questions:
Is PGP encryption secure?
Yes, it is secure. Although the software is more than twenty years old, there don’t exist any vulnerabilities. No one finds any vulnerabilities in the basic implementation of the system. It implies that encrypting the emails isn’t enough for total security. It is better always to use this software along with a full cybersecurity suite. This suite should include threat detection software.
What is the best PGP software?
The best software relies on which purpose you do want. In most cases, people don’t need to encrypt emails. Therefore, for all of them, a web-based Pretty Good Privacy email provider is the best solution. However, you should download a software add-on for your email client when you need to send emails frequently which have to be encrypted.
Do I need encryption software?
A: It depends on the person. When you have to store customer information, you must need this encryption software. You don’t need to encrypt your personal files. What you can do is improve your defenses against a cyberattack. Always start working with that encryption software that is based on Pretty Good Privacy software. It is very easy to work with you. Besides, this one is a good place to start encrypting files.
It can be a powerful tool to protect your data, privacy, as well as security. This one is a completely secure method of sending emails. Besides, it also helps to identify people with whom you are communicating. As most email clients prefer to use the add-ons of this software, it is very simple to implement.
Secure email is a part of cybersecurity. Along with the software, you should also use a robust data security platform and Data Loss Prevention software. The perfect way to make sure of security and privacy is to use a wide range of tools as much as possible.
How do you get your PGP public key?
To get the PGP public key, what you can do is to go to a keyserver like hkp://subkeys.pgp.net or ldap://keyserver.pgp.com. Whether you are unable to get access to a Keyserver or don’t have access to this, you need to save the whole Pretty Good Privacy Software block into a file. Hence, you need to tap on the Grab option.
How do you copy a PGP public key?
First, you need to go to the Desktop page of this software. Then, you have to tap on the “PGP Keys”. After that, you need to right-click on it to export. Next, you have to choose the “Copy Public Key” option.